|
|
Prevention Starts with Perception
|
|
Unparalleled prevention of all attacks across email, web browsers and cloud collaboration apps
|
|
Perception Point is a Prevention-as-a-Service company, built to enable digital transformation.
Trusted by global enterprises, it's Gartner-recognized, revolutionary platform offers a
360-degree protection against any type of content-based attacks, across all collaboration channels,
in one simple solution. Built by and for IT and security experts, the service is incredibly easy to deploy,
maintain and update according to the newest attack techniques.
|
|
Security Solution
|
|
Any Threat. Any Channel Lightning Fast Detection
|
|
Perception Point's solutions protect all organizations by isolating,
detecting and remediating any cyber threat that is delivered via text,
files and URLs, across email, web browsers, cloud apps and collaboration channels.
|

|
|
Eliminate Security Blind Spots with 360° Channel Coverage
|
|
Organizations are exposed to external and insider threats from email,
web browsers and other cloud collaboration channels. Perception Point holistically
protects your main attack vectors, allowing you to easily extend the same policies,
consolidate and simplify security systems, and obtain a unified solution that isolates,
detects and remediates all threats in the organization.
|

|
|
Advanced browser-based detection and isolation lets your users access the web without
exposing enterprise data to risk
|
|
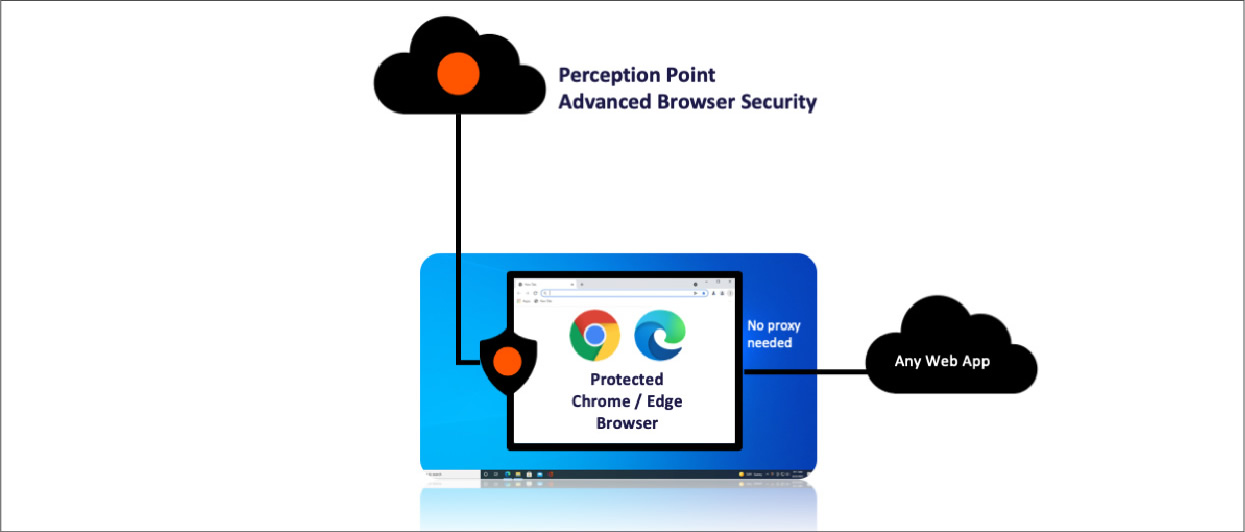
Perception Point Web Security is easy to deploy, with a browser extension for advanced
detection capabilities or a secure web browser with a light agent, adding VM-based
isolation to Chrome/Edge on Windows or Mac. You can prevent all threats from the web and
ensure enterprise apps are accessed via a trusted Chrome/Edge Enterprise browser.
|
|
|
Protect Your Organization with Unprecedented Advanced Threat Detection
|
|
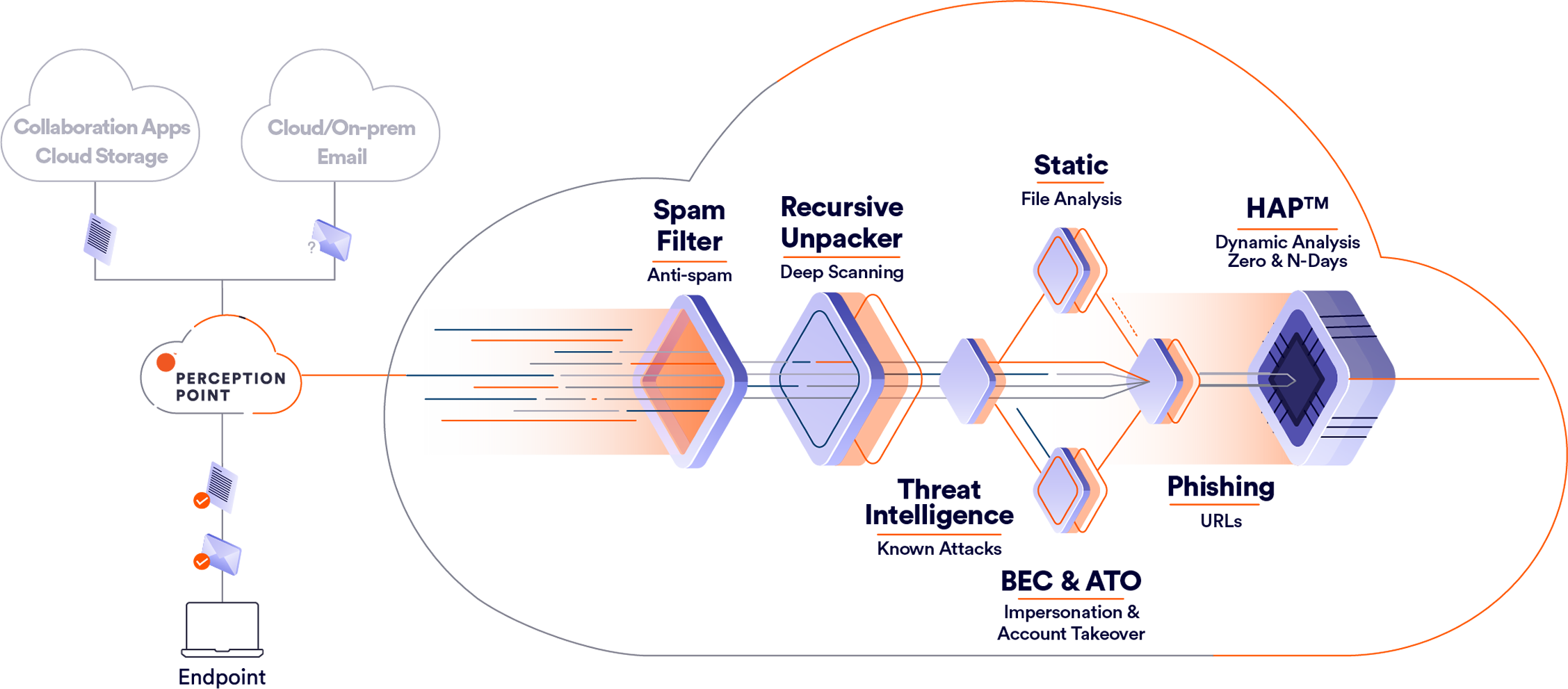
Perception Point is a pioneer in advanced threat detection. Our platform recursively
unpacks every piece of content and rapidly scans all text, files and URLs with multiple
advanced detection engines. The different engines leverage state of the art detection algorithms
using computer vision, machine learning, and various dynamic and static methods, to intercept every
type of threat, from commodity attacks to advanced threats.
|
|
|
1. Spam Filter (Email Only)
Receives the email and applies reputation and anti-spam filters to quickly flag an email as malicious.
|
2. Recursive Unpacker
Unpacks the content into smaller units (files and URLs) to identify hidden malicious attacks, extracting embedded URLs and files recursively by unpacking files and following URLs. All of the extracted components go separately through the next security layers.
|
3. Threat Intelligence
Combines multiple threat intelligence sources with our internally developed engine that scans URLs and files in the wild to warn about potential or current attacks.
|
4. Phishing Engines
Combines best-in-class URL, reputation engines and an in-house image analysis engine to identify impersonation techniques and phishing attacks.
|
5. Static Signatures
Combines best-in-class signature based antivirus engines together with proprietary technology to identify highly complicated signatures.
|
6. BEC
Prevention of payload-less attacks that don't necessarily include malicious files/URLs, eg. spoofing, look-alike domain, display name deception.
|
7. HAP™ (Hardware-assisted Platform)
Next-gen sandbox proprietary engine that is composed of software algorithms using CPU-level data to access the entire execution flow, right from the processor, to deterministically intercept any type of advanced attack on both Windows and macOS environments. This layer provides unprecedented detection against malicious code execution in scripts and executable files, zero-day and N-day vulnerabilities, logical bugs, next-gen exploitations, ATO and more.
|
|
|
Resources
|
|
|