 |
Protect Your Data
And Your Peace of Mind
|
|
When it comes to cybersecurity, the landscape is full of single-solution providers,
making it easy for unexpected cyberthreats to sneak through the cracks.
At Fortra, it is creating a stronger, simpler strategy for protection.
One that increases customers’ security maturity while decreasing the operational burden
that comes with it. This is all possible thanks to it’s best-in-class portfolio and deep
bench of expert problem solvers.
|
|
Data Security Solution
|
|
Digital Guardian
|
|
Protect sensitive data on all your endpoints
|

|
Digital Guardian Data Loss Prevention:
Protect Sensitive Data on ALL Your Endpoints
|
The Digital Guardian Data Protection Platform, powered by AWS, performs on
traditional endpoints, across the corporate network, and on cloud applications,
making it easier to see, understand, and protect your sensitive data.
Cloud-delivery simplifies deployment, cross-platform coverage eliminates gaps,
and flexible controls stop the riskiest behavior without impacting productivity.
Digital Guardian gives you the deployment flexibility to match your enterprise
needs, whether SaaS, fully managed, or on-premises.
|
 |
Cloud-Delivered
Powered by AWS, Digital Guardian delivers simplified deployment, low overhead, and elastic scalability for increased return on investment
|
 |
Cross Platform
Coverage for your Windows, macOS, or Linux operations systems and all your applications, both browser based and native
|
 |
Flexible Controls
Fine-grained controls, ranging from log & monitor to automated blocking, help protect data before it’s lost
|
 |
Deepest Visibility
See everything that happens to organization’s sensitive data
|
 |
No Policy, No Problem
“Risk discovery” approach enables organization to see where sensitive data is located, how it flows, and where it is out at risk - all without policies.
|
|
|
Titus
|
|
The foundation of data security
|
|
|
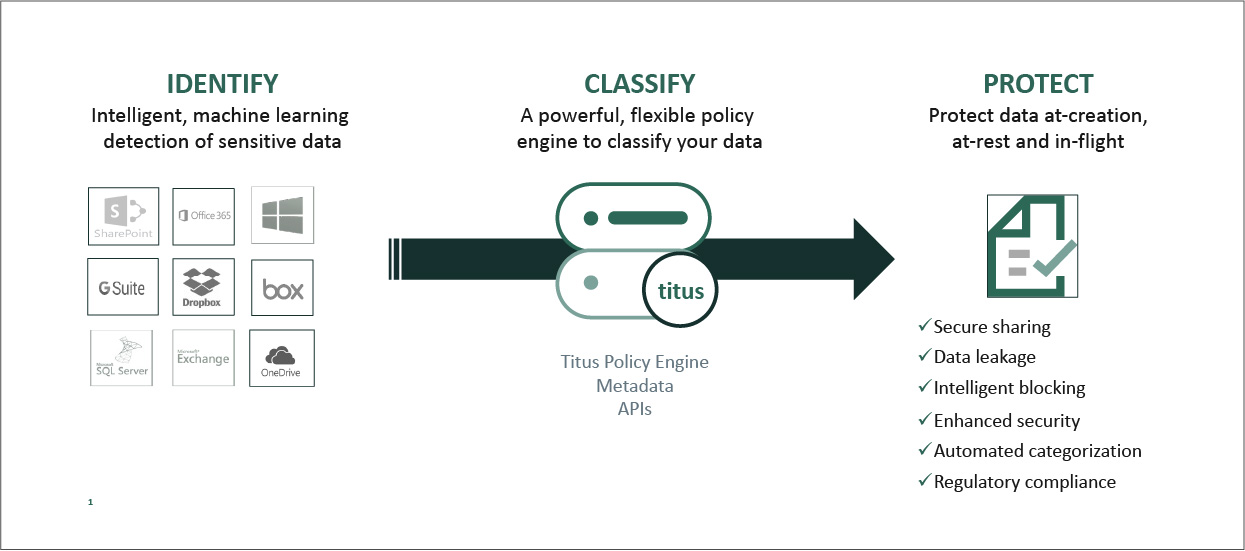
Titus data classification enables organizations to truly understand what kind of data they possess,
the value of that data, and how best to classify files in order to mitigate exposure to risk.
With Titus, you can clearly and accurately classify emails, spreadsheets, presentations, and other file
types using user selected, system-suggested, or automatically applied classification settings that are
based on your unique data security policies. It is designed to empower employees to work confidently and
productively, with the knowledge that their emails, documents, and sensitive information are all protected.
|
 |
Titus Classification Suite
Add rich context to on-pem and cloud data with data classification
|
 |
Titus Illuminate
Scan and analyze unstructured data at rest and apply appropriate identification attributes
|
 |
Titus Identifiers for Privacy
Detect personally identifiable information (PII) at creation in email and files. Powered by Machine Learning
|
 |
Titus Encryption
Combine data classification and encryption into a single flexible data proetction solution
|
|
|
Vera
|
|
Powerful data protection, anywhere
|
|
|
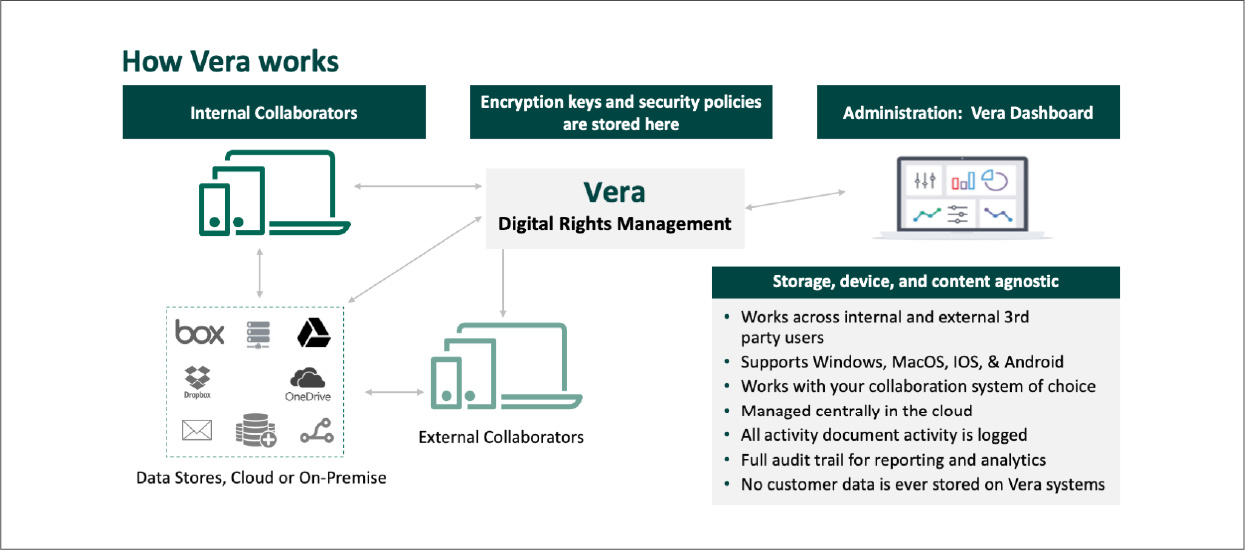
Vera makes it easy to securely share files externally with third parties, providing you
control over file access and protection wherever data travels. Secure, track, audit,
and revoke access to your crown jewels, including sensitive financial and legal data,
so that your most sensitive content stays protected. With robust policy enforcement,
strong encryption, and strict access controls, Vera’s data-centric security solution
enables teams to collaborate freely while ensuring the highest levels of security, visibility, and control.
|
 |
SECURE
Automatically secure your sensitive data when it’s shared internally and externally.
|
 |
TRACK
Track every time data is accessed throughout its lifecycle.
|
 |
AUDIT
Mitigate compliance risk with full audit trail.
|
 |
REVOKE
Revoke access to sensitive data and files shared with departing employees and 3rd party providers.
|
|
|
Agari
|
|
Robust DMARC Authentication and Monitoring Solution
|
|
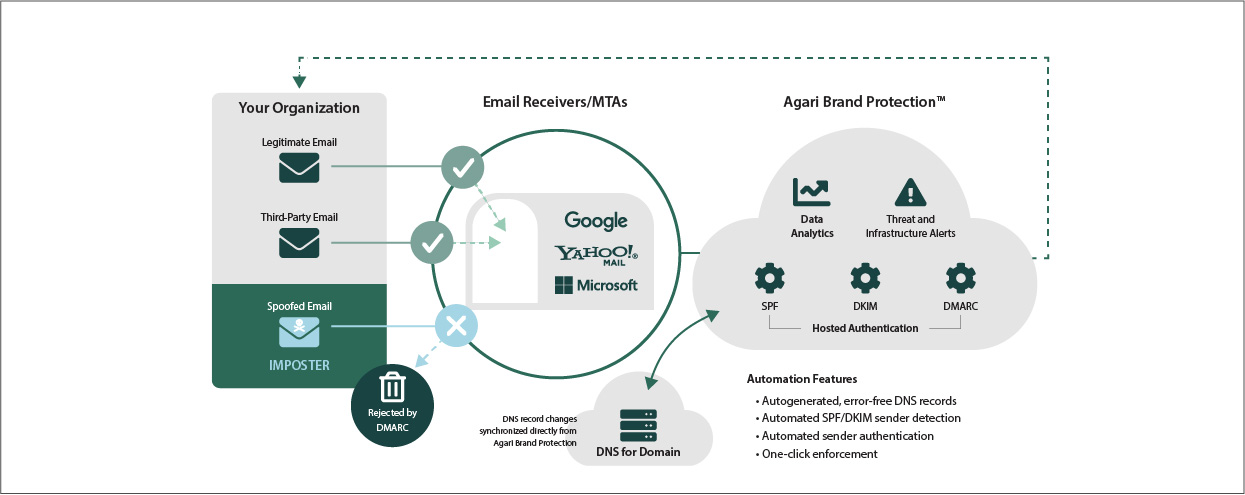
It takes years to build trusted relationships with your customers - but cybercriminals
can abuse that trust to trick your customers into opening their malicious emails in a matter of minutes.
DMARC is an essential email authentication protocol that enables administrators to prevent
hackers from hijacking your domains for email spoofing, executive impersonation, and spear
phishing. But email is complicated and getting email authentication correct is criticial,
so that only the spoofing is blocked.
Agari Brand Protection simplifies DMARC management at every level, helping organizations to
protect their customers and partners from email attacks that hijack their brand through:
|
 |
Authentication
Provides insight into ALL legitimate email sources for full authentication.
|
 |
Conformance
Ensures all third-party senders conform to your email standards.
|
 |
Reporting & Analytics
Aggregates DMARC data by leveraging AI and data science.
|
|
|
Infrastructure Protection Solution
|
|
Digital Defense
|
|
Vulnerability Management and Penetration Testing Services
|
|
Originally developed as a Software as a Service (SaaS) security platform,
Frontline.Cloud provides robust yet easy to deploy security solutions that deliver
unparalleled results. Frontline.Cloud lifts the administrative burden associated with
on-prem and hybrid security solutions while offering the best discovery and analysis
technology in the industry. A variety of options are available:
|
 |
Frontline VM™
Vulnerability Management
|
 |
Frontline WAS™
Web Application Scanning
|
 |
Frontline ATS™
Active Threat Sweep
|
 |
Frontline Pen Test™
Online Reporting
|
|
|
Core Impact
|
|
Pen Testing Software
|
|
Core Impact is an easy-to-use penetration testing tool with commercially developed and tested exploits that enable security team to exploit security weaknesses, increase productivity, and improve efficiencies.
|
| • |
Provides visibility into the effectiveness of organization’s defenses
|
| • |
Reveals where most pressing risks exist
|
| • |
Utilizes a stable, up-to-date library of commercia-grade exploits and real-world testing capabilities
|
| • |
Replicates attacks across network infrastructure, endpoints, web, and applications to reveal exploited vulnerabilities
|
|
|
Cobalt Strike
|
|
Adversary Simulation & Red Teaming
|
|
Cobalt Strike is a robust threat emulation tool that allows security professionals and Red Teams to replicate advanced attacks and put incident response strategy to the test to enhance security.
|
| • |
Enables security teams to replicate the same tactics and techniques of today’s cyber criminals
|
| • |
Provides a flexible framework designed to be extended and customized by the user community
|
| • |
Fosters Red Team collaboration by sharing data and allowing communication in real-time
|
| • |
Generates reports to provide a complete picture of the engagement
|
|
|
Resources
|
|
|


